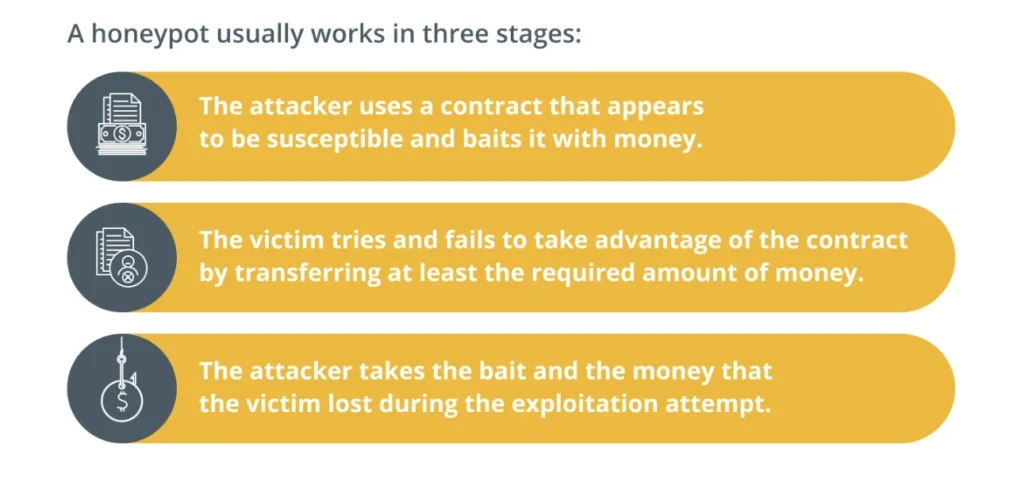
TL;DR
What is a honeypot crypto? It’s a smart trap in the crypto world, using smart contracts on blockchains like Ethereum to catch attackers. These traps can look like easy targets but are designed to protect crypto assets and gather data on hackers.
There are different types, like pure, high-interaction, mid-interaction, and low-interaction honeypots, each serving unique roles in cybersecurity. Spotting a honeypot scam involves looking for tokens that are easy to buy but hard to sell and using tools like Etherscan to investigate.
While honeypots offer valuable security insights and early attack detection, they’re not foolproof and require careful management to avoid being turned against the organization.
They’re a critical part of a broader security strategy to safeguard against crypto scams and attacks, enhancing the security of crypto exchanges, wallets, and investors in the ever-evolving crypto industry.
What is a Honeypot Crypto?
Honeypots Explained Simply
Imagine a big pot of honey that’s really a trap. In the crypto world, a honeypot is like this but for catching bad guys.
It’s a smart trick using smart contracts on blockchains like Ethereum. These contracts look like they have a mistake, making attackers think they can steal crypto.
But it’s a setup! When they try, the trap catches them instead.
Also read: How to Create a MEV Bot in 2024 – A Comprehensive Guide
The Inner Workings of a Crypto Honeypot
Here’s how it works: A honeypot smart contract pretends to have a flaw. It might look like anyone can take some Ethereum (ETH) if they just send a little bit of ETH first.
But when someone tries to grab the ETH, a hidden trap stops them. The trick is, the honeypot focuses on one mistake so the attacker misses the trap waiting for them.
This way, only the person who made the honeypot can get the ETH out. It’s a clever way to catch attackers in the act.
Honeypots are not just about catching attackers. They also teach us about the tricks scammers use. This helps make the crypto space safer for everyone.
But remember, not all traps are easy to spot. That’s why it’s super important to be careful in the crypto world. Always check things out before you send crypto or trust a contract.
Types of Honeypots in Crypto
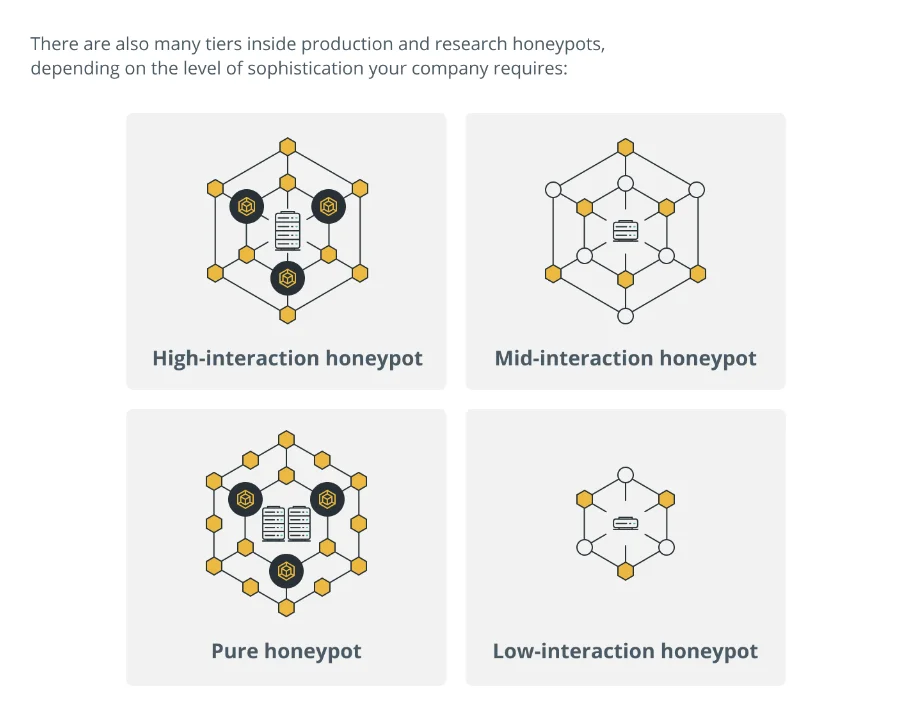
In the crypto world, honeypots are clever traps set to catch attackers. But not all honeypots are the same.
They come in different types, each with its own way of working. Let’s dive into the main types and see how they trick the bad guys.
Research vs. Production Honeypots
- Research Honeypots are like detectives. They’re set up to gather info on attackers. By watching how attackers try to break in, these honeypots help us understand their tricks. This info is super helpful for making the crypto space safer.
- Production Honeypots are like decoys. They’re put in places where attackers might try to strike. Their job is to distract attackers from real targets. This way, they protect valuable crypto assets and keep the attackers busy.
Different Levels of Trickery
- High-interaction honeypot is the most complex. They pretend to be real systems with lots of services. Attackers can dig deep, thinking they’re hitting the jackpot. But in reality, they’re just showing their hand.
- Mid-interaction honeypots act like they have real apps but no deep system underneath. They’re there to confuse attackers, giving security pros time to catch them.
- Low-interaction honeypots are the simplest. They mimic just a few services to catch attackers early on. They’re easy to set up and great for a quick alert on possible attacks.
- Pure Honeypots are full-scale traps, loaded with fake data and sensors. They’re tough to manage but give the richest info on how attackers work.
Each type of honeypot plays a unique role in the crypto security world. From gathering intel to directly protecting assets, honeypots are key players in keeping the crypto industry safe from attackers.
By understanding how different honeypots work, we can better protect ourselves and our crypto journey from the many tricks out there.
Also read: Discover the Best Place to Stake Ethereum: Top 5 Platforms for Ethereum Staking
Spotting a Honeypot Scam in Crypto
In the crypto world, not everything that glitters is gold. Honeypot scams are sneaky traps set to catch unwary crypto enthusiasts.
Knowing how to spot these scams is crucial for protecting your assets. Let’s dive into how you can identify a honeypot scam and keep your crypto journey safe.
How to Tell if It’s a Trap
Honeypot scams in crypto are cleverly disguised to lure you into making a move you’ll regret. One major red flag is a token that seems too easy to buy but impossible to sell.
This is a classic honeypot trap: it tempts you with the promise of easy profits, only to lock your funds away.
Another sign is the trade history of the token. If you notice lots of buys but no sells, or if sells are only successful for certain wallet addresses, you might be looking at a honeypot.
These scams exploit the decentralized nature of blockchains like Ethereum, using smart contracts to create traps.
Tips to Avoid Falling Victim
Protecting yourself from honeypot scams requires vigilance and a bit of detective work:
- Do Your Homework: Before investing in any crypto project, research thoroughly. Check the project’s website, its presence on social media platforms, and any community discussions.
- Use Blockchain Explorers: Tools like Etherscan for Ethereum or BscScan for Binance Smart Chain can help you investigate a token’s contract and transaction history.
- Look for Audits: A legitimate project will often have its smart contract audited by a reputable firm. Lack of an audit is a red flag.
- Watch Out for Red Flags: Be wary of projects with anonymous teams, unrealistic promises of high returns, or a very recent launch date.
- Use Common Sense: If something seems too good to be true, it probably is. Trust your instincts and avoid deals that promise the moon without any risk.
By staying informed and cautious, you can navigate the crypto space more safely and avoid falling prey to honeypot scams. Remember, in the world of cryptocurrency, knowledge is not just power—it’s protection.
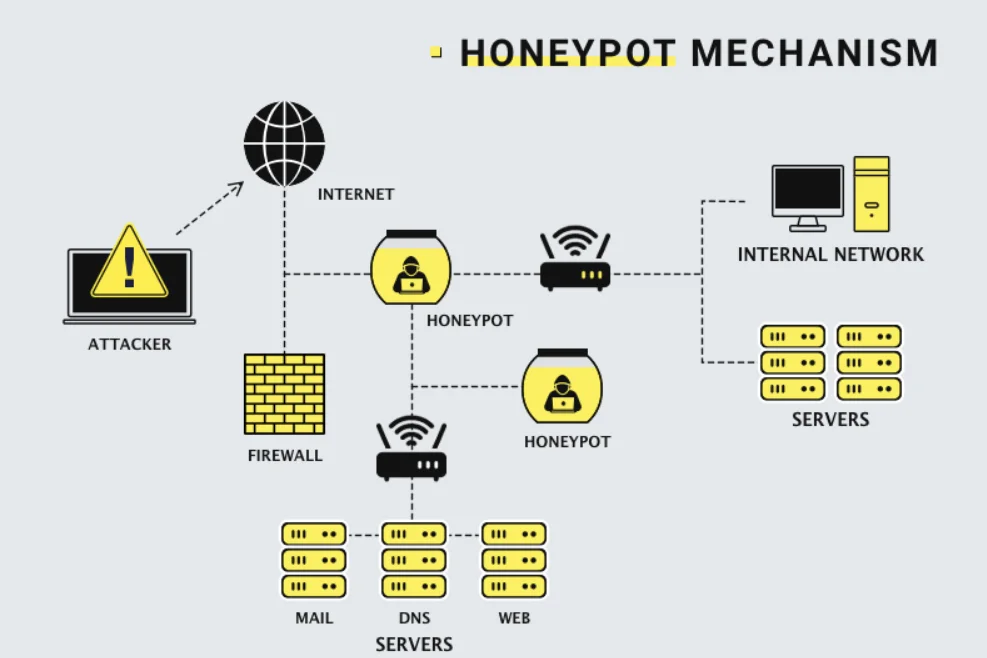
The Pros and Cons of Honeypots
Honeypots are a fascinating part of cybersecurity, acting as decoys to lure cyber attackers. By pretending to be real systems, they can trap hackers and study their methods.
This dual role makes honeypots invaluable in the fight against crypto scams and attacks. However, like any tool, they have their strengths and weaknesses.
Why Honeypots Are Good
Honeypots are great for several reasons. First, they help detect attacks early, giving security teams a heads-up before real damage occurs.
They’re like alarm systems, alerting when something fishy is happening. Also, honeypots can collect valuable data on how attackers operate. This information is gold for improving security measures.
By understanding the tactics of hackers, cybersecurity professionals can better protect crypto wallets, exchanges, and smart contracts from future threats.
Also read: What is Bitcoin Skimming: Unveiling the Revolutionary Profit Strategy
But, They’re Not Perfect
Despite their benefits, honeypots aren’t without flaws. One major downside is that they only capture data when attacked. If hackers don’t bite, there’s no insight gained.
Plus, there’s always a risk that a savvy hacker might recognize a honeypot and use it against the organization, either by avoiding it or, worse, turning it into a tool for launching further attacks.
Additionally, setting up and maintaining honeypots requires resources and expertise. They need to be convincing enough to attract attackers but secure enough to prevent any real harm.
In essence, while honeypots can be powerful allies in cybersecurity, relying on them alone isn’t wise. They should be part of a broader security strategy that includes various measures to protect against crypto scams and attacks.
By balancing their pros and cons, organizations can make the most of what honeypots have to offer in safeguarding the crypto industry.