TL;DR
Keypoints to Remember:
- Always Download from Trusted Sources: Get your crypto mining software only from reputable websites or the official GitHub page to avoid malware.
- Monitor Your System’s Performance: High CPU usage might signal unauthorized mining on your computer.
- Add Mining Software to Antivirus Exceptions: Prevent legitimate mining programs from being blocked by adding them to your antivirus’ whitelist.
- Stay Informed on Security Practices: Regular updates and security measures can protect you from the latest cryptojacking attempts.
- Use Dedicated Hardware for Mining: This minimizes the risk of malware spreading to your personal files and ensures efficient mining operations.
In the digital gold rush, where bitcoin and other cryptocurrencies reign supreme, mining software plays a crucial role. But not all that glitters is gold. Sometimes, what seems like a tool to earn cryptocurrencies turns out to be a trap.
This article dives into why crypto mining software flagged as malware, mistaking it for malware. From hijacked CPUs and GPUs mining Monero or Ethereum without your consent to hackers using your system resources for their gain, we’ll cover it all.
We’ll also guide you on distinguishing genuine miner software from malicious ones, ensuring your mining journey is both safe and fruitful.
Whether you’re a seasoned miner or just starting, understanding these challenges and how to overcome them will make your crypto mining venture worthwhile.
Also read: Can You Mine Crypto on a Virtual PC? Unveiling the Possibilities and Challenges
Exploring the World of Crypto Mining Software
Dive into the complex and fascinating world of crypto mining software, where the digital gold rush meets modern technology.
Here, we unravel the intricacies of mining software, distinguishing the good from the malicious, ensuring you navigate this landscape with knowledge and safety.
Introduction to Cryptocurrency Mining
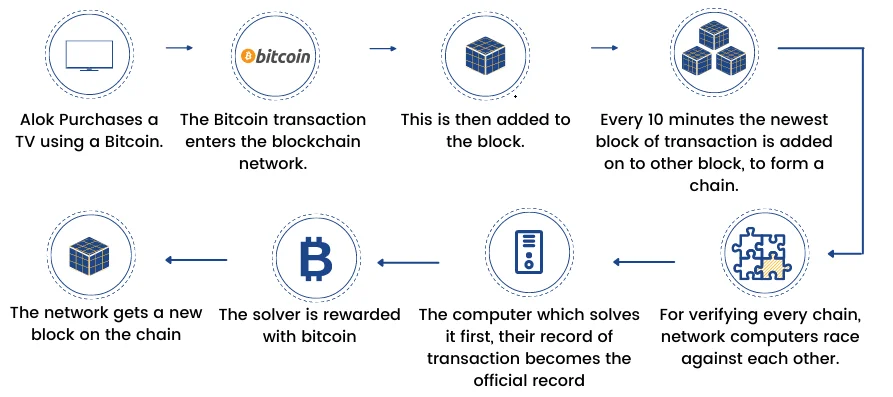
Cryptocurrency mining is the backbone of blockchain technology. It uses computational power from CPUs and GPUs to solve complex mathematical problems, validating transactions on a blockchain.
This process not only secures the network but also creates new cryptocurrencies, rewarding miners for their efforts. Mining software, essential for this task, can range from simple, user-friendly applications to complex systems requiring dedicated hardware for mining.
The Legitimacy of Crypto Mining: A Double-Edged Sword
While mining cryptocurrencies like Bitcoin and Monero is a legitimate way to earn digital currency, it’s not without its pitfalls. Genuine mining activities require explicit permission to mine, using one’s own or shared computational resources in a mining pool.
However, the lucrative nature of cryptocurrencies has attracted cryptojackers—malicious actors who secretly mine cryptocurrency without the victim’s knowledge, hijacking computer resources and greatly increasing CPU and GPU usage, often leading to unauthorized mining.
Identifying and Differentiating Malicious Mining Software
Spotting malicious mining software is crucial to protect your digital assets and computing resources. Look for these signs:
- High CPU Usage Without Consent: If your system’s CPU and GPU usage spikes dramatically without your direct activity, it might be mining cryptocurrencies without your permission.
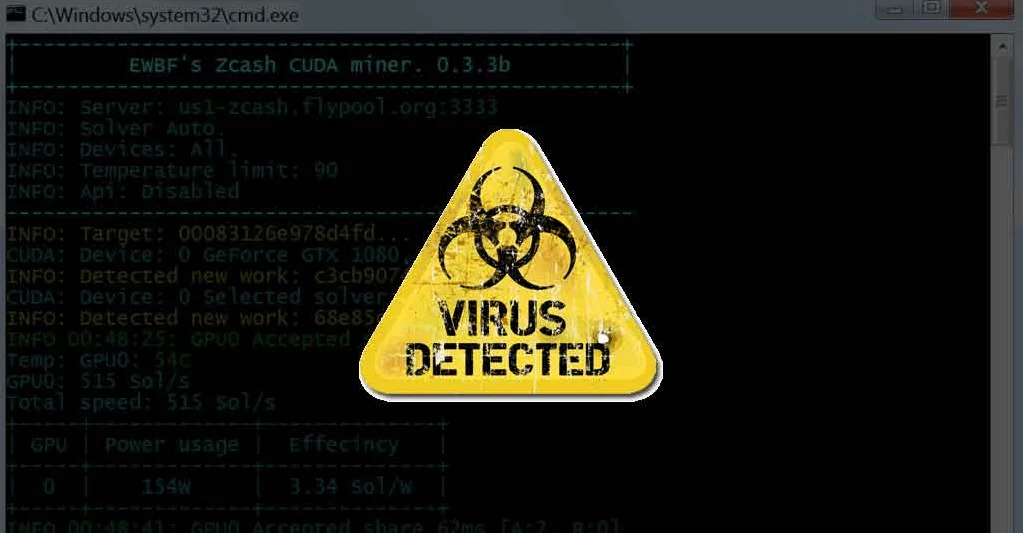
- Programs Get Flagged by Antivirus: Windows Defender and other antivirus programs block mining software, often labeling them as potential threats due to their similarities with known malware forms.
- Unexpected System Slowdowns: A sudden decrease in your computer’s performance could indicate unauthorized mining software running in the background.
- Suspicious Executables: Be wary of software that you didn’t download from a trusted source like the official GitHub page or direct from the mining software’s website. Always verify the authenticity through Virus Total.
- Phishing and Ransomware Risks: Malicious software may try to steal private details or encrypt your data for a ransom. Legitimate mining software will never ask for sensitive information.
Understanding these aspects of crypto mining software ensures you stay informed and can confidently distinguish between beneficial mining operations and those intending to exploit your system’s resources.
Navigating the Challenges: Mining Software vs. Antivirus Software
Tread carefully in the battleground where mining software and antivirus programs clash. Understanding why antivirus software often misidentifies mining applications as threats and how to navigate these waters can be crucial for anyone looking to mine cryptocurrencies safely.
Why was crypto mining software flagged as malware?
Antivirus programs are designed to protect your PC from threats that can compromise your security or utilize your resources without permission. They flag mining software as malware for several reasons.
Historically, cryptojackers have abused mining software to use victims’ computational power for their own gain, often embedding cryptojacking malware in seemingly benign applications.
This unauthorized mining drains system resources, leading to high CPU usage and system instability, characteristics similar to many malware forms.
Consequently, antivirus software, in an effort to protect users, may produce false positives, mistakenly identifying legitimate mining programs as threats.
Strategies to Prevent Legitimate Mining Software from Being Flagged
To ensure your mining software runs smoothly without being halted by antivirus software, consider these strategies:
- Add Exceptions: Add your mining software to the antivirus’ exception list, explicitly allowing it to run on your system.
- Use Verified Sources: Always download mining software from verified sources, such as the official project website or a well-known GitHub page, to avoid instances of mining malware.
- Keep Software Updated: Ensure both your mining and antivirus software are up to date. Developers often address compatibility issues in updates.
Dealing with Cryptojacking: Detection and Prevention
Cryptojacking, where attackers use your computer to mine cryptocurrency without your knowledge, poses a significant risk. Detect and prevent it by:
- Monitoring System Performance: An unusual spike in CPU usage can indicate cryptojacking. Regular monitoring can help detect unauthorized mining activities.
- Install Security Software: Use reputable antivirus and anti-malware programs that specifically include cryptojacking detection capabilities.
- Stay Informed: Being aware of the latest cryptojacking techniques and malware can help you stay one step ahead of attackers.
Ensuring Safe Crypto Mining: Best Practices and Security Measures
In the vast ocean of crypto mining, navigating safely requires more than just a good map; it demands a sturdy ship, a knowledgeable captain, and a vigilant lookout. Here, we outline the best practices and security measures essential for safeguarding your mining journey against the turbulent waters of online threats.
Choosing the Right Mining Software: Safety First
The first step in safe mining is selecting the right software. Not all mining applications are created equal, and the difference between a secure operation and a compromised system often lies in the software choice. Here’s how to ensure safety first:
- Verify Sources: Always download mining software directly from reputable sources, such as the official website or a trusted GitHub page. This reduces the risk of encountering malware disguised as mining software.
- Research: Before starting mining, spend time researching your chosen software. Look for reviews, user experiences, and any reports of suspicious behavior.
- Compatibility Check: Ensure the software is fully compatible with your system to avoid unnecessary strain on your processing power, which can mimic the effects of cryptojacking malware.
Optimizing Your Mining Operations for Safety and Efficiency
Optimizing your mining setup not only improves efficiency but also enhances safety. Follow these steps to optimize your operations:
- Dedicated Hardware: If possible, use dedicated hardware for mining to isolate and protect your personal data. This separation minimizes the risk of malware spreading from your mining operations to personal files.
- Monitor Performance: Regularly monitor your system’s performance for signs of unauthorized access or high CPU usage, which could indicate malware activity.
- Update Regularly: Keep your mining software and system’s operating system updated. Developers often release security patches in new updates to protect against known vulnerabilities.
Future-Proofing Your Mining Endeavors Against Malware Threats
The crypto mining landscape is ever-evolving, with new malware threats emerging regularly. To future-proof your mining operations:
- Stay Informed: Keep abreast of the latest in crypto mining and security. Understanding new threats and the tactics of cryptojackers allows you to adjust your defenses proactively.
- Use Security Software: Employ comprehensive security software that includes features specifically designed to detect and prevent cryptojacking and other forms of malware.
- Secure Your Network: Ensure your mining network is secure. Use strong passwords, enable two-factor authentication where available, and consider using a VPN for an added layer of security.
By adopting these best practices and security measures, you can protect your mining operations from unauthorized access and malware, ensuring a productive and safe mining experience. Remember, in the world of crypto mining, safety and vigilance are as valuable as the cryptocurrencies you’re working to mine.
Conclusion: Balancing Mining Efficiency with Cybersecurity
In the journey of crypto mining, knowing how to navigate the waters safely is crucial. From choosing the right software to protecting your system from cryptojackers, each step is vital to ensure a fruitful mining process.
Remember, not all that glitters in the digital mine is gold. Some are traps set by hackers aiming to use your processing power for their gain. By staying informed and vigilant, using trusted sources for your mining software, and securing your network, you can shield yourself from unauthorized mining and malware.
Whether you’re mining Bitcoin with NiceHash or solving complex mathematical problems with Xmrig, the key to success lies in safe practices. Keep your private details secure, and let your computer’s processing power work for you, not against you.